How to remove CryptoClone Ransomware and decrypt .crypted files

Threat's profileName of the threat: Command or file name: Threat type: Affected OS: CryptoClone Ransomware (randomname).exe Ransomware Win32/Win64 (Windows XP, Vista/7, 8/8.1, Windows 10) 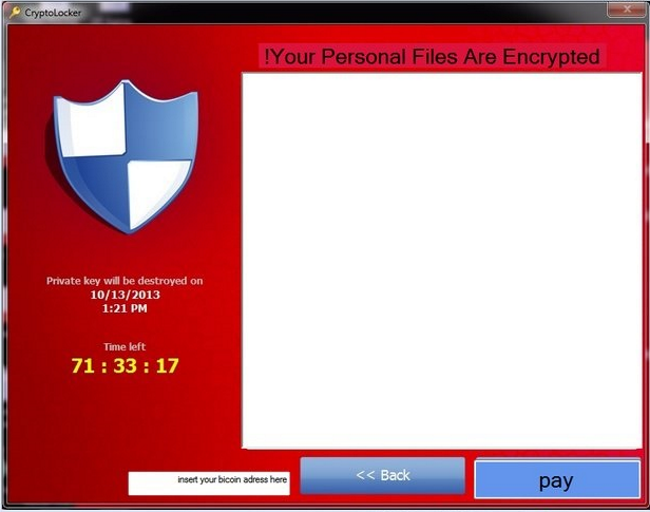
CryptoClone Ransomware intrusion methodCryptoClone Ransomware copies its file(s) to your hard disk. Its typical file name is (randomname).exe. Then it creates new startup key with name CryptoClone Ransomware and value (randomname).exe. You can also find it in your processes list with name (randomname).exe or CryptoClone Ransomware. Also, it can create folder with name CryptoClone Ransomware under C:\Program Files\ or C:\ProgramData. If you have further questions about CryptoClone Ransomware, please, contact our technical support. It is free. Or you can use programs to remove CryptoClone Ransomware automatically below. Download Wipersoft AntispywareDownload this advanced removal tool and solve problems with CryptoClone Ransomware and (randomname).exe (download of fix will start immediately): Download WiperSoft Antispyware to remove CryptoClone Ransomware* WiperSoft Antispyware was developed to remove threats like CryptoClone Ransomware in automatic mode. Remover has active module to protect PC from hijackers, trojans, ransomware and other viruses. Trial version of Wipersoft provides detection of computer viruses for FREE. To remove malware, you have to purchase the full version of Wipersoft. Features of WiperSoft Antispyware
Download Spyhunter Remediation Tool by Enigma SoftwareDownload antimalware designed specifically to remove threats like CryptoClone Ransomware and (randomname).exe (download of fix will start immediately): Download AntiMalware to remove CryptoClone RansomwareFeatures of Spyhunter Remediation Tool
Let our support team solve your problem with CryptoClone Ransomware and remove CryptoClone Ransomware right now! 
Submit support ticket below and describe your problem with CryptoClone Ransomware. Support team will offer you solution in several minutes and give a step-by-step instruction on how to remove CryptoClone Ransomware. Trouble-free tech support with over 10 years experience removing malware.  Threat's description and solution are developed by Security Stronghold security team. Here you can also learn:
How to remove CryptoClone Ransomware manually?This problem can be solved manually by deleting all registry keys and files connected with CryptoClone Ransomware, removing it from starup list and unregistering all corresponding DLLs. Additionally missing DLL's should be restored from distribution in case they are corrupted by CryptoClone Ransomware. However, this threat may not allow you to do htis in some cases, thats why, we recommednd you to use one of the above options. To get rid of CryptoClone Ransomware, you should: 1. Kill the following processes and delete the appropriate files:
Warning: you should delete only those files which checksums are listed as malicious. There may be valid files with the same names in your system. We recommend you to use WiperSoft Antispyware Malware Remediation Tool for safe problem solution. **Trial version of Wipersoft provides detection of computer viruses for FREE. To remove malware, you have to purchase the full version of Wipersoft. 2. Delete the following malicious folders:
3. Delete the following malicious registry entries and\or values:
Warning: if value is listed for some registry entries, you should only clear these values and leave keys with such values untouched. We recommend you to use WiperSoft Antispyware Malware Remediation Tool for safe problem solution. How to decrypt .crypted files after CryptoClone Ransomware infection?You may attempt to decrypt files infected by different versions of CryptoClone Ransomware manually. Modern ransomware threats use complex encryption algorithms and try to prevent users from decrypting their files by disabling System Restore option, removing Shadow copies and previous versions of user files. However, in most cases, there is still a chance to restore your files using one of the described metods. There is also special advanced data recovery software, that can revive lost data in several clicks. This is not a guarantee for data restoration, but it is worth giving a try. Using advanced data recovery software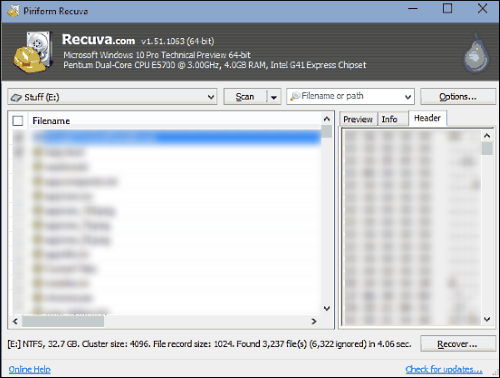
Restore encrypted files using System RestoreSystem Restore constantly creates copies of files and folders before major changes in the system (windows update, software installation). You can also create restore point manually from time to time. CryptoClone Ransomware may remove system restore files, but you can check it using following instruction. 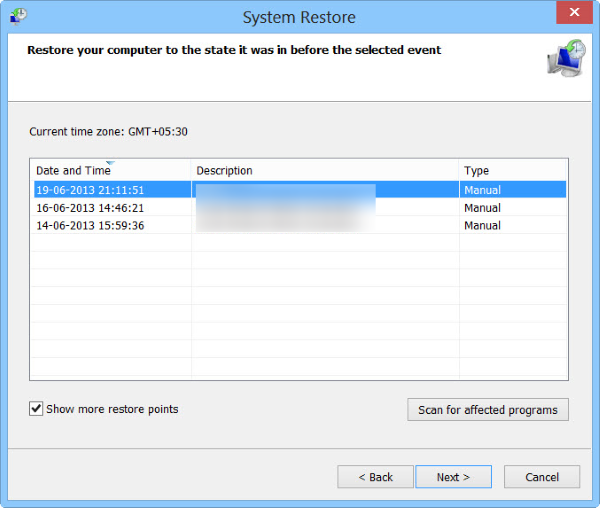
Roll the files back to the previous versionPrevious versions are copies of files and folders made by Windows Backup (if Windows Backup option is turned on) or copies of files and folders created by System Restore. You can use this feature to restore files and folders that you accidentally modified or deleted, or that were encypted by CryptoClone Ransomware. Available only in Windows 7 and later versions. 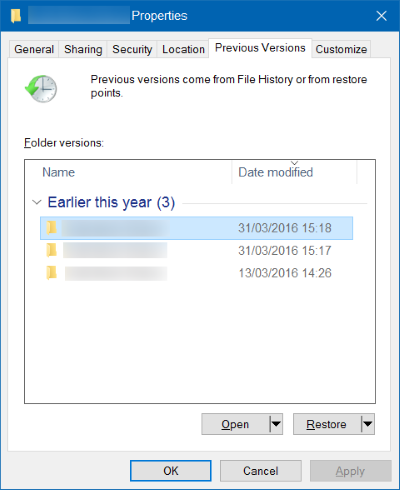
Restore .crypted files using shadow copies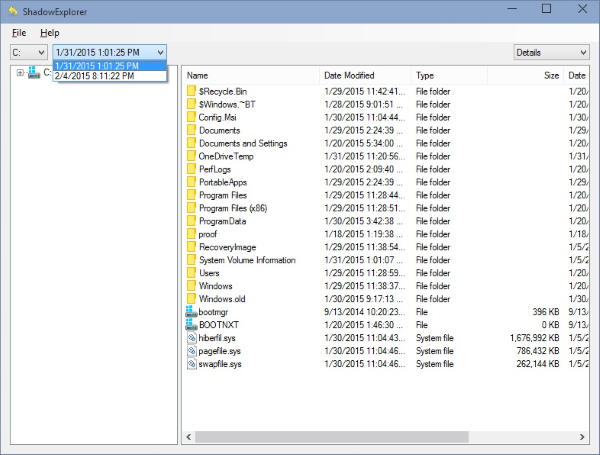
Protect your computer from ransomwareMost of modern antivirus solutions have a module to protect from ransomware threats. However, there are also special solutions, that can detect cryptoviral activity and stop it, preventing modification of your files. One of the best is ZoneAlarm Anti-Ransomware utility, that will not use much resources for effective protection against latest ransomware threats. 
Information provided by: Aleksei Abalmasov |
Copyright © 2026 Security Stronghold. All Rights Reserved. All content on this website is protected and belongs to Security Stronghold LLC.



